August 25, 2019 / by Adam Murray / In security
Security 101: Get back to basics with asset management
Many companies are splashing out on the latest and greatest security products, but they’re often overlooking the fundamentals. For example, if you ask your operational teams how many Windows hosts you have, do you get a consistent answer? Take the following all-too-familiar tweet:
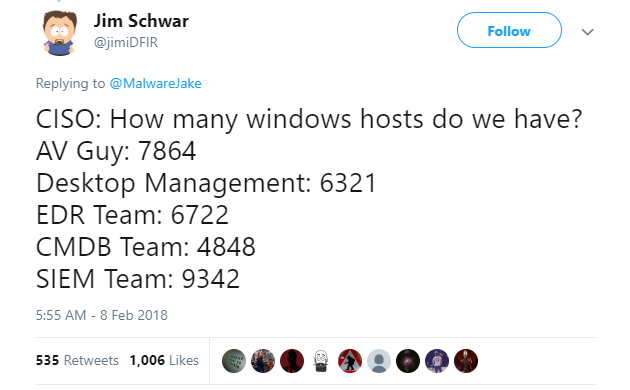
We see countless companies with similar varied responses. It’s not surprising, then, that the Center for Internet Security (CIS) prioritises the top two security controls as:
- Inventory and control of hardware assets
- Inventory and control of software assets
When we meet customers initially, most don’t have control of their assets and consequently have large gaps in their security posture. If you have an unpatched Windows server humming away with disconnected Domain Admins RDP sessions or running a service under an account that’s a Domain Admin, then a potential attacker has an easy vector to owning your whole domain. If you don’t have a system in place that accurately reports on the assets in your environment, then you’re likely flying blind.
Once you have an accurate list of your assets, you can then correlate the data with existing security controls, such as patch management or vulnerability management solutions, and begin to identify gaps in your environment.
To maintain accurate data, these systems can’t rely on human updates – they need automation. Also, if your company has a configuration-management database (CMDB) and you’re not using automation to populate the data, there’s a good chance that the data in it is outdated and inaccurate, and it may be giving you a false sense of security.
Do you assign owners to devices, and do they regularly revalidate why those devices exist? Do you know who the infrastructure support team is, the app support team, and the business owner? Are you looking at the full life cycle of the device from design, to operational life, to decommissioning? We see many servers that were built for projects that never went ahead but that remain turned on years later. This scenario not only increases the attack surface of your environment, but also means additional running costs for your business.
The keys to accurate asset management are automation and ownership. If you can get data from a system, don’t let people alter that data. People should be responsible only for the pieces of information that systems can’t gather – for example, a device description or who the owner is. Automation should move the device through its life cycle – again, until it’s decommissioned. For example, if a server is stale in Active Directory, automation should set the device to inactive.
You also need a system in place to facilitate human revalidation. Every 90 days, send owners a link so they can view their devices and easily update the owner and description fields. If they don’t action the request, the system needs to escalate this inactivity to their manager. To do this, you need a way to get accurate organisation information.
See where you stand today. Ask the teams within your organisation how many Windows hosts they have. You might be surprised, and it might be time to do something about it.
If you need a hand, we can help you get back to basics. Feel free to contact us on info@tikabu.com.au.